Project update 11 of 15
Talos FPGA Functions and Responsibilities - Part 1
We have received a large number of inquiries regarding the open-toolchain FPGAs in use on Talos™, and their function within the Talos™ system. In this update, we begin to explore the functions and responsibilities handled by these FPGAs, and the associated technology used to secure the Talos™ systems.
Overview
Like the vast majority of modern computers, Talos™ incorporates a low pin count (LPC) bus that is used for a variety of low-level functions, including firmware access, TPM access, SuperIO communication, and Intelligent Platform Management Interface (IPMI) communication. Unlike any other computers currently in existence, Talos™ contains our exclusive LPC Guard™ and FlexVer™ technologies, which prevent LPC bus snooping / hijacking and allow for flexible, owner-controlled verified boot, respectively. These technologies are driven by dedicated FPGAs and are auditable / user modifiable via the associated BSD-licensed Hardware Definition Language (HDL) files. LPC Guard™ is covered in detail at the end of this update, while FlexVer™ is the subject of a future update. In addition, the Lattice iCE40 FPGAs used exclusively on Talos™ have an open toolchain available via the IceStorm project, which allows Talos™ to self-host its reprogrammable logic components and assures the integrity of the resultant bitstreams.
GPIO
One of the more widely known functions handled by the FPGAs on Talos™ is the GPIO interface. As shipped, the GPIO FPGA is a dedicated device that allows each GPIO line to be configured as input or output, as well as read or written, over the LPC bus. Interrupts are supported via the LPC SIRQ function, and our LPC Guard™ technology ensures that this device can be safely reprogrammed while the Talos™ system is online and operational. Potential uses for this device include an atomic clock interface using the PPS functionality of the kernel, a high-speed parallel interface to an external peripheral, or even simple control of chassis fans, lights, or coolant pumps via PWM and an external driver board. With Talos™, you are in full control of the hardware — no hacks or reverse engineering required!
LPC IRQ Routing
POWER8 devices require a small amount of LPC traffic modification, specifically interrupt merging, to function correctly. Talos™ uses a small portion of logic in one of its FPGAs to perform this minor task, versus the proprietary CPLD used on other OpenPOWER systems.
Power Sequencing and Peripheral Control
Off-die peripheral power gating, reset handling, and other peripheral control functions are implemented in soft logic on Talos™, along with the interface to the chassis lights / switches. This allows for significant future flexibility in researching new power saving methods, as well as the potential for bug fixes or other modifications to, for example, work around non-standards-compliant third-party add-on peripherals. Most existing mainboards use dedicated TTL and discrete transistor logic for these functions, and on more than one occasion this has forced a new PCB revision to fix compatibility issues with third-party add-on components. With Talos™, a simple update of the FPGA firmware is all that would be required!
Base System Security
Talos includes a number of security features in addition to the LPC Guard™ and FlexVer™ systems. On Talos™, the machine owner can set switches to write protect either parts of or the entire Flash ROM, for each Flash ROM present. Furthermore, the BMC can be isolated from one or both of the on-board network interfaces, using additional configuration switches on the main security switch block. The on-board FPGAs handle these isolation functions, and furthermore the current hardware security state can be read directly from the hardware via LPC, allowing additional anti-tamper verification for secure applications. Finally, the entire system is protected by our exclusive owner-controlled FlexVer™ technology, which will be detailed in a future update.
LPC Guard™
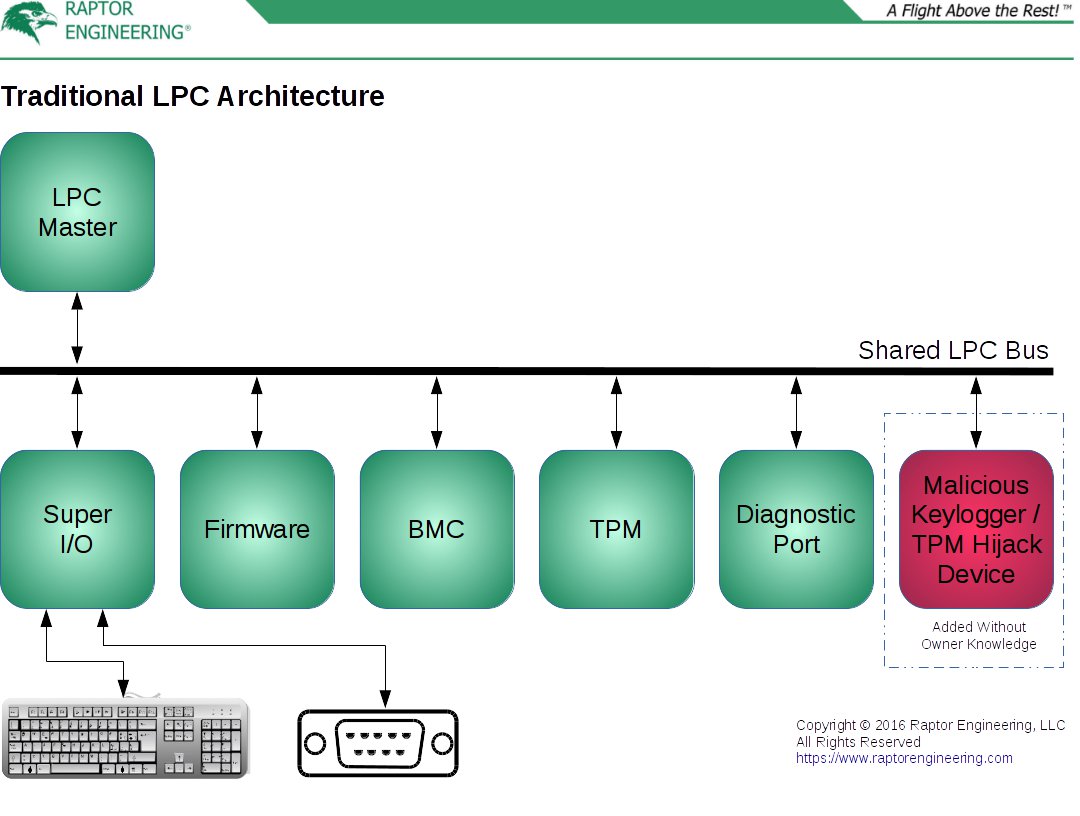
One of the more interesting features of Talos™ is our LPC Guard™ technology. The LPC bus is a shared, bidirectional bus that often handles highly sensitive traffic such as TPM transaction cycles, password entry via PS/2 keyboard, and low level firmware read / write cycles. All existing systems using LPC for these functions share a single, fatal flaw. Since the LPC bus is shared, a malicious peripheral can be surreptitiously attached to the LPC interface without detection, then transmit interesting information read directly from LPC out of band to an attacker, e.g. over Bluetooth or another wireless link, or even store the interesting information for later physical retrieval. Due to the simplicity of the LPC bus, it is trivial to, for instance, implement a keylogger using inexpensive and miniature components, one that will not be detected outside of a thorough physical inspection of the mainboard.
Even worse, the LPC bus is prone to hijack. Exploits exist in the wild to monitor and override the TPM control signals simply by attaching a small hijacking device to the shared LPC bus, resulting in the TPM receiving "correct" measurements and unsealing keys even when the CRTM or system in general has been compromised with malicious firmware and/or software. These two issues combined effectively render any existing system using LPC permanently vulnerable to extremely effective, inexpensive, fast, and easy physical attack without the owner’s knowledge. This, in turn, prohibits deployment of said systems in environments the owner does not physically control when trusted computing is required, and also indicates that any existing co-located systems relying on an LPC TPM for security should not be considered trusted.
What is LPC Guard™?
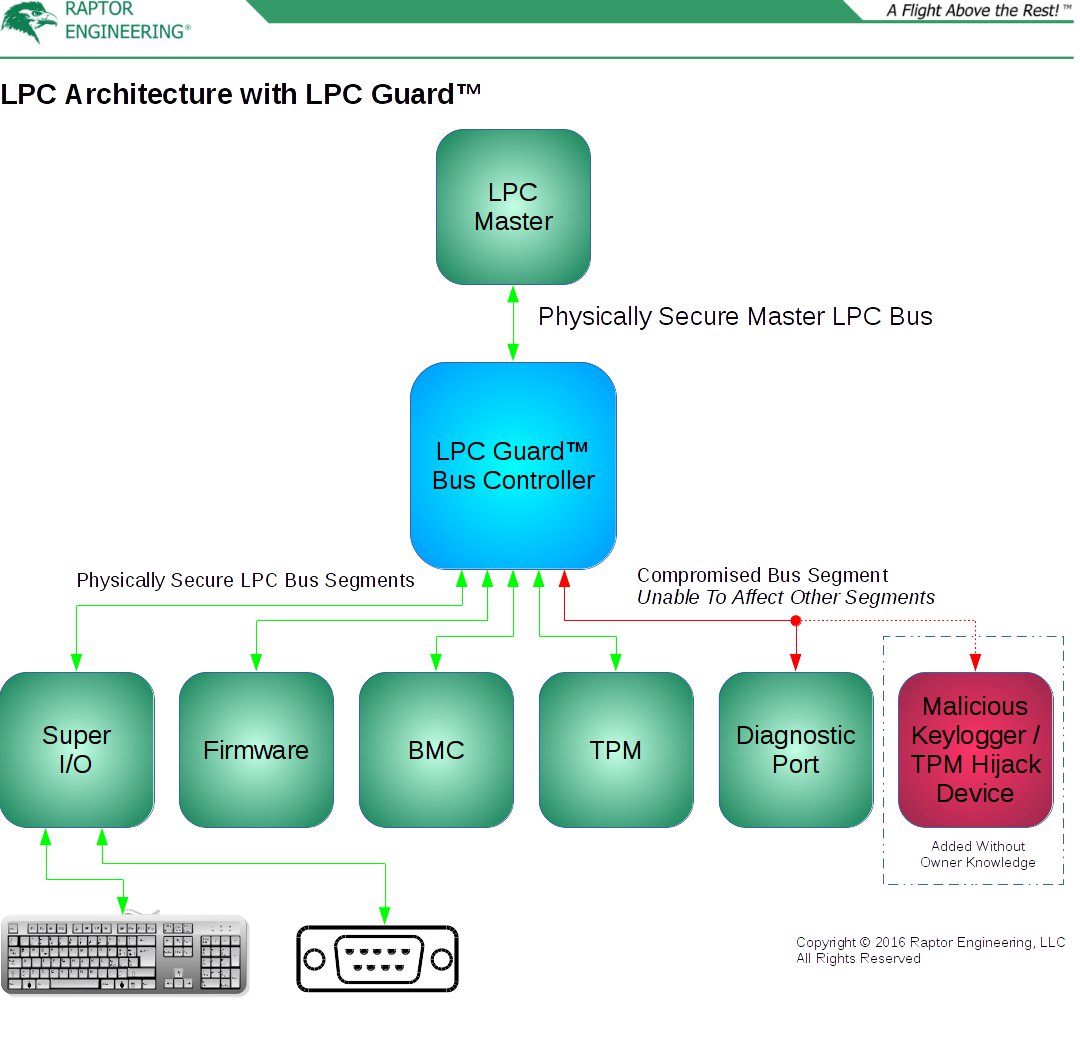
In a nutshell, LPC Guard™ converts the traditional monolithic shared LPC bus topology into a pseudo-star topology, then masks sensitive data transmissions involving a single peripheral from all remaining peripherals on the bus. The bus control device central to this technology is securely connected to the LPC master onboard the CPU or southbridge device, with the associated PCB traces located in central layers of the system board. All LPC peripherals attach directly to this bus control device, thus allowing the bus controller to modify all data and control signals being sent to and from the LPC master and each peripheral. From the perspective of the LPC master and peripherals, the normal shared LPC bus is logically present, although it is not physically present. This modification does not alter LPC compatibility in any way. For additional security, sensitive peripherals also securely connect to the bus controller, with the associated PCB traces located in central layers of the system board.
How Does It Work?
In most situations, LPC data is transferred between the LPC master and a single peripheral. LPC transactions are framed, with control lines used to initiate, control, and end a transaction. Each frame contains header information including the destination address and whether the LPC master or the peripheral will be transmitting data. The bus controller monitors these frames, and listens for the headers while broadcasting all control and data information to all peripherals and the LPC master. When it detects an LPC master-directed transmission from a peripheral, for example from the keyboard controller inside the SuperIO, the bus controller replaces incoming data from the keyboard controller with dummy data for transmission to the LPC’s other peripherals. The incoming data from the keyboard controller is passed unmodified to the LPC master, and all control lines continue to be broadcast to all peripherals and the LPC master for the duration of the transaction. Due to this alteration of the broadcast data, a malicious peripheral attached to the bus will not be able to snoop on the keyboard controller data, blocking LPC keyloggers from working without direct physical attachment to the bus segment in question.
LPC transmissions from the master to a peripheral are normally less sensitive, however there are still some instances where a malicious device could pull valuable data by monitoring peripheral-directed transmissions, such as during a firmware update if key material is contained within the firmware image. To mitigate this, the bus controller contains a routing table with LPC addresses mapped to physical ports. This routing table is configured in early system setup via its host-only LPC peripheral interface, and is used to mask data to all peripherals except the pre-configured destination peripheral for the given address or address range.
Finally, the bus controller includes LPC bus recovery logic. If a peripheral drops off one of the LPC ports, for instance the GPIO FPGA, the bus controller is able to finish any open transaction with dummy data in order to restore bus functionality. This avoids a hard system freeze and requisite reboot in case of recoverable (i.e., non-system-critical) LPC peripheral malfunction.
Bus Hijack Mitigation
LPC Guard™ only provides partial protection against the TPM bus hijack attack mentioned earlier. It makes hijack far more difficult, requiring physical removal of either the TPM chip or bus controller on properly designed mainboards, as opposed to the simple, hot-pluggable connection to mainboards without LPC Guard™, but it does not stop a determined attacker with access to an offline system for an extended period of time. LPC Guard™ is intended to be used in conjunction with FlexVer™, which provides the remaining mitigation against TPM bus hijacking as well as unauthorized bus controller modification. We will explore FlexVer™ in a future update, so stay tuned!
Conclusion
From exclusively using open-toolchain FPGAs to providing auditable security components and a reconfigurable GPIO interface, Talos™ is likely the most secure, auditable, and extensible general purpose workstation / server system ever marketed. Talos™ respects your freedom and privacy, not only through open firmware components and owner-controlled trusted computing, but also through the ability to modify the operation of Talos™ and its external interfaces at an unprecedented level. If you want to help reverse the trend of vendor-controlled and locked machines, please purchase a Talos™ mainboard, system, or POWER8 SSH access today!