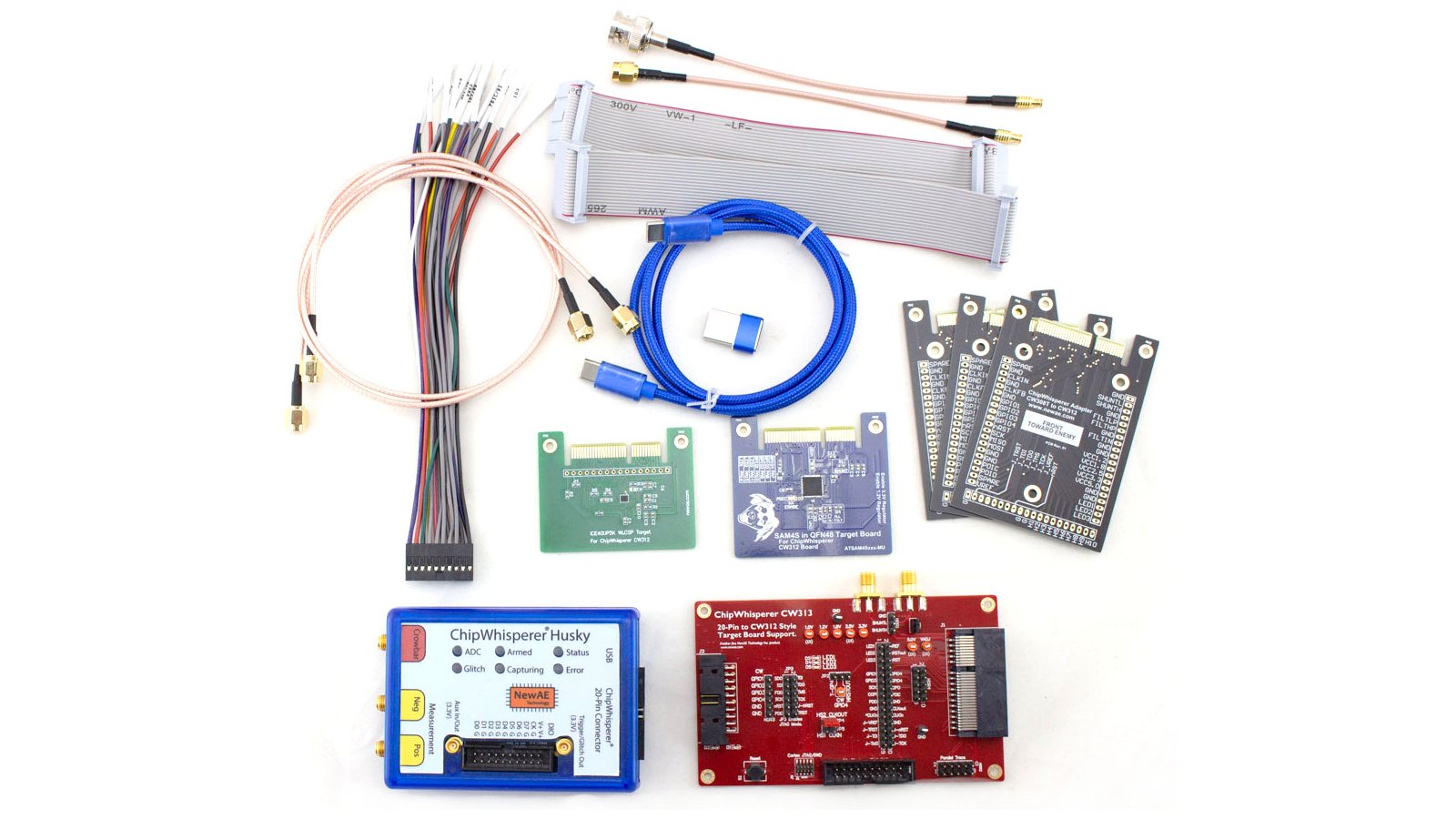
ChipWhisperer-Husky Starter Kit
Run most of the ChipWhisperer tutorials, including power analysis, clock glitching, and voltage glitching. Includes ChipWhisperer-Husky unit, CW313 target base-board, iCE40 (small FPGA) target, SAM4S (Arm processor) target, USB cables, SMA cables, 20-pin straight-through and breakout cables

Hardware Crypto Target Pack
A selection of targets with hardware cryptographic features, which allow you to perform more advanced power-analysis attacks, includes SAM4L, SAM11L, EFR32MG32A, and MK82F. Targets are in both CW308 and CW312 form factors.
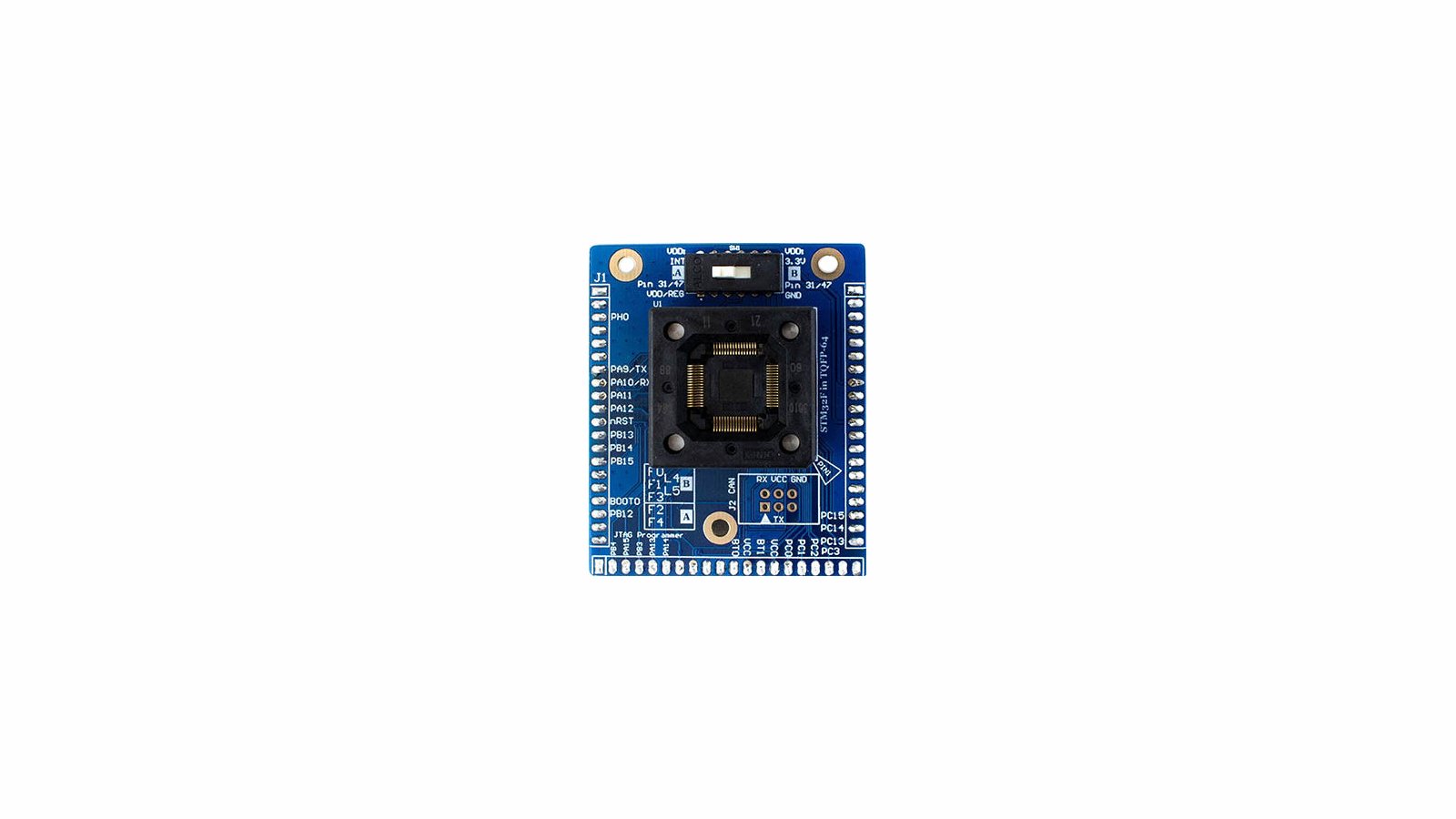
CW308 STM32F Socket Target
A TQFP64 socket that fits most STM32F0/1/2/3/4 microcontrollers (along with GigaDevice compatable pinouts). Great for performing research on multiple devices and testing how resiliant templates are.