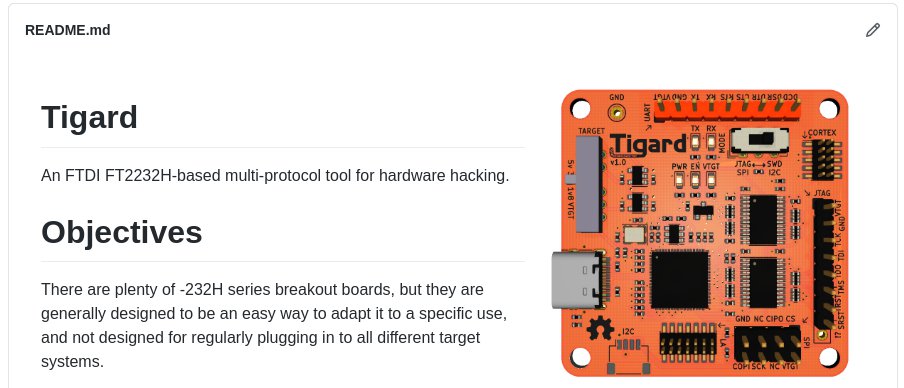
I’ve spent most of the last decade teaching hardware hacking and hardware security techniques. Tigard was designed first and foremost as a tool to enable my training. By extension, it’s well suited to plenty of real-world uses as well, which is why we opted for this CrowdSupply campaign as well.
Whether you’re pledging $39 or $1337, I think you deserve decent documentation and some tutorials on how to use Tigard. This week, I’ll start by explaining a little bit of my training philosophy, then I’ll outline what will be available for training and documentation, and finally, I’ll wrap up with a bit about the economics of running a training business.
Training Philosophy
I’ve written before about my training philosophy, but I’d like to focus why we even need training and tutorials in the first place.
If you’re already familiar with UART, serial consoles, and embedded systems, and you already had an objective in mind, you might be able to pick up a tool like Tigard, glance at the documentation, and put it to use. Since you know what you want to do, the documentation should spell it out for you.
Have you ever looked at a tool’s documentation, wanting to learn how to use it, but were completely confused? That’s not your fault - the documentation assumed you already knew why you were using the tool and just needed to know the right procedure. In all fairness, this does keep the tool’s documentation concise and topical.
It does, however, present a problem: You have to understand what a tool (like Tigard) is capable of to understand how techniques (like speaking to a serial console) might be useful… all in order to understand why it fits into a broader tactic (like manipulating sensitive files via that console).
Tigard Resources
We’ve got a chicken-and-egg problem, and one size doesn’t fit all - that’s why we plan to have a variety of different resources about using Tigard that might make sense based on your experience and background.
Documentation
Are you a seasoned hardware hacker? Did you know exactly how you could use Tigard as soon as you heard about it? Then Tigard’s documentation is for you. You’ve already got the tactics and techniques under your belt, you just need to know the exact pinouts, switch setting or command line parameters to get the job done.
HowTo Videos in Updates
If you don’t have all that background understanding, the videos included in previous updates are a good starting point. I don’t cover how things work or why you might want to do them - but give a pretty concise example of what you could do with Tigard.
Applied Physical Attacks on Tigard
Soon (most likely before you get Tigard in your hands) I’ll post a free Applied Physical Attacks with Tigard course.
My objective is to cover both the what and the how of using Tigard - both the tool and the techniques behind it. I’ll cover all the core features of Tigard with video demonstrations, followed by step-by-step procedures that you can follow using Tigard along with readily available target systems (both microcontrollers and single board computers)
Again - this is free for anyone. Most of the instructions will also work fine with the Adafruit, FTDI, or CJMCU breakout boards. I will even encourage you to re-use the material to teach others the techniques.
Applied Physical Attacks on Embedded and IoT Systems
While the $1337 pledge level does include a few extra pieces of hardware, it isn’t about getting your hands on LEET hardware hacking gear - it’s all about leveling up your LEET hardware hacking skillz with access to Applied Physical Attacks on Embedded and IoT Systems. This is the course I have been teaching in person for several years, updated for online, self-paced delivery. All together, it covers 4 full days of instruction (32 CPEs if you’re counting), and in that time I hope that attendees get as much out of it as they would from spending a full month of self-study.
For this course, each topic includes a video lecture, followed by a procedure to follow. There are hints, a full walk-through, or a followup explanation for each lab. By taking the time to go in-depth on each topic, we are able to answer why the tools and techniques are relevant and how they fit together into sound hardware hacking tactics. By repeating several techniques, we reinforce and solidify the understanding behind them and fully comprehend the capabilities of the tools.
I’d like to reinforce that this course isn’t about Tigard. It does use Tigard as a means to an end - but it is my objective that you’d complete the course with a firm enough background understanding that you’re able to adapt to whatever tool is available or most suited with a quick read of it’s documentation.
Running a Training Business
Tigard is my first real physical ‘product’. For 8 years, SecuringHardware.com has offered hands-on hardware hacking and hardware security training almost exclusively. I do this because I truly enjoy teaching - the difficulty is making training a commercially viable business without depending on or being distracted by consulting work. I’ve done this by making sure the value of my training is measurable in the amount of time it saves versus paying employees to self-study the same level of understanding.
While this helps me run a profitable business with enough margin to finance projects like Tigard, it is frustrating to me that my core training is inaccessible to people without corporate training budgets. In the past I’ve tried to balance this by offering free workshops at conferences and other events, and this has worked well - but does not scale well, and does not translate to the current travel/gathering reality.
As I continue to bring my existing (paid) multi-day courses online, I hope to compliment them with shorter, freely available workshops. My hope is that not only with this teach a much larger audience, but that others will use the material to help teach others. I hope to have the Tigard-focused workshop available soon, and will follow it with similar courses covering Bitmagic/Pulseview and more.
I’ll finish this week’s update with a quick look at the Applied Physical Attacks toolkit and course website: