PhyWhisperer-USB is moving along! This week we wanted to show off some of the features added recently to the tool. You can always check out the bleeding-edge from the active GitHub repository.
API taking shape
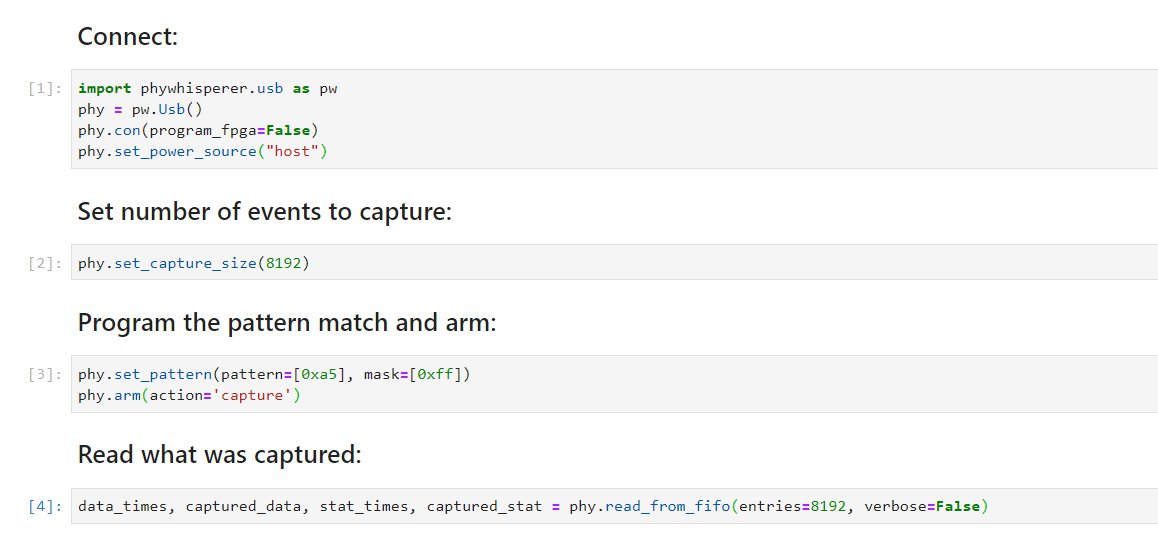
While low-level access to the FPGA control registers is still available, higher-level functions for common tasks are now available too. This example sniffs 8192 events when it sees a data byte of 0xa5 (‘events’ include data, timestamps, and USB status updates such as ‘rxerror’).
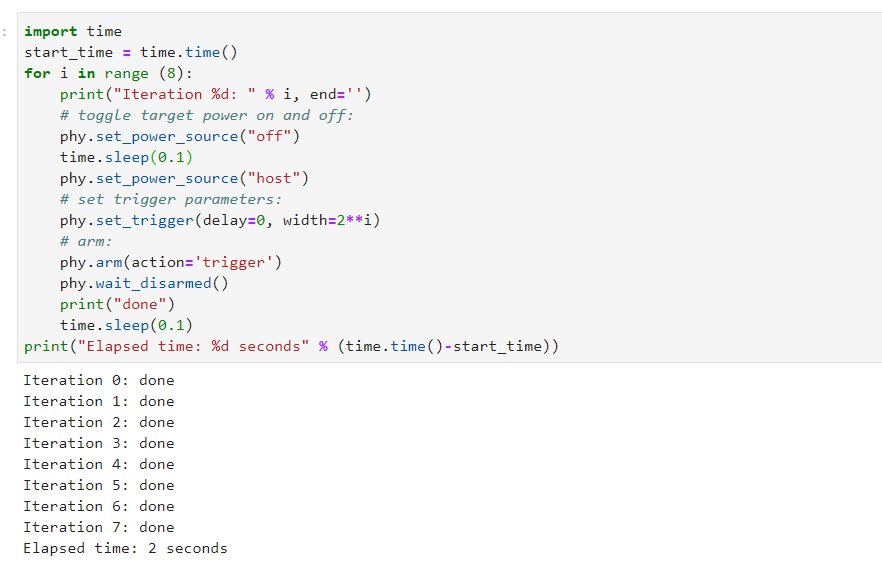
This next example shows how PhyWhisperer can be used to trigger the injection of a glitch with varying parameters, resetting the target between each glitch:
You’ll also need some hardware to inject the glitch. From outside you can see our prototype unit (sans enclosure) power cycling a target of interest here:
Fast capture speed
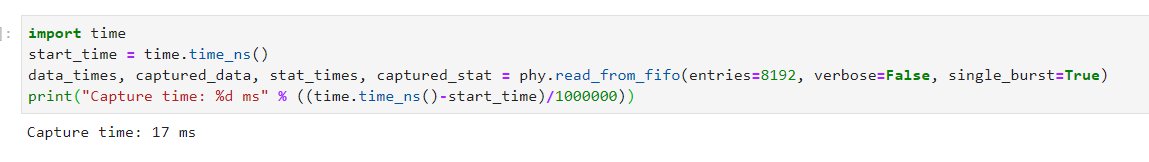
Capture is fast! The entire capture buffer of 8192 entries can be read in a single burst in milliseconds:
Concurrent capture
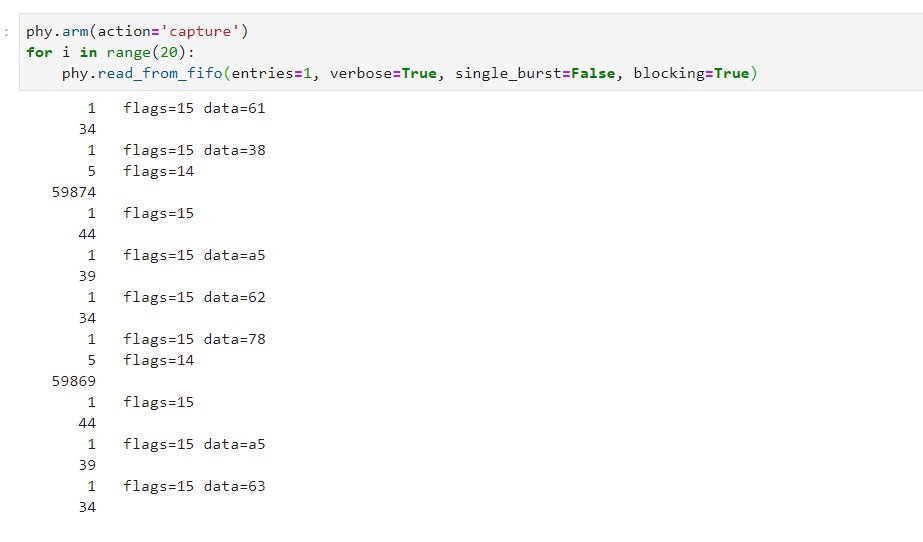
Alternatively, it’s also possible to read data one entry at a time, as it’s coming in:
As before, this can be piped into a decoding logic in order to visualize the traffic itself. We’ll be showing how various open-source frontends can be connected directly to PhyWhisperer-USB in a future update.
Automatic detection of USB PHY speed
The PhyWhisperer-USB supports all three USB 2.0 speeds (low speed, full speed, and high speed). The USB 2.0 LS/FS and HS have different logic levels, so you previously needed to tell the analyzer which to monitor. That isn’t necessary now as PhyWhisperer-USB can now automagically detect a target’s speed by passively observing the negotiation between the target device and the host:
These features show the majority of logic already working for PhyWhisperer-USB, and we haven’t even finished the campaign yet! So once we get hardware into your hands, you can expect things to come pretty close to "just working" without delay.