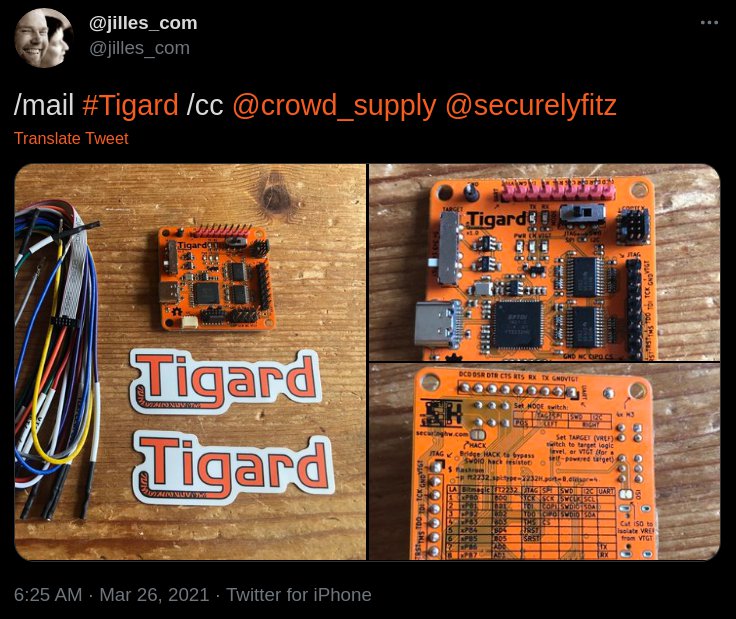
Delivered!
I’ve been stalling for this update, hoping to have some substantive information to share on delivery. While everything shipped to the distributor last month, I haven’t had any visibility into where they are in the pipeline.
As of last week, nearly all of the campaign orders have shipped. There have been a few hiccups, but for the most part they’re getting into everyone’s hands:
Now What?
Let’s go through the resources available to help you use Tigard:
Documentation
The best first place to look for Tigard information is the README in the repository. There, you can find tables of all the pinouts you should use for all the different protocols supported, as well as code snippets and command examples for getting and using existing software for each of the protocols.
If you see any issues with the documentation, or even just have feedback, the best way to share it is by filing an issue on Github. I am planning on refactoring it a bit in the near future, but i’d love to do that after getting a little bit of feedback on what’s there now and what, if anything, is missing.
Workshop
The "Applied Physical Attacks using Tigard" Workshop is still in progress, but rather than finish it up behind a wall, I’ve opened access to it. There are video demos as well as instructions and examples for various used of Tigard. As I mentioned in my Tools and Training update - the REAMDE might be fine if you know what you want to do, and just need to know how to do it. This workshop is intended to take a step back, and start by showing what you can do.
Field Reports
You’ve got Tigard in your hands - you’ve got hardware hacking challenges in front of you - we’d all love to hear what you’re working on. You can submit a field report on Crowd Supply’s website. These are helpful for us to understand how Tigard is useful to you - and we hope to feature a few of them in future updates.
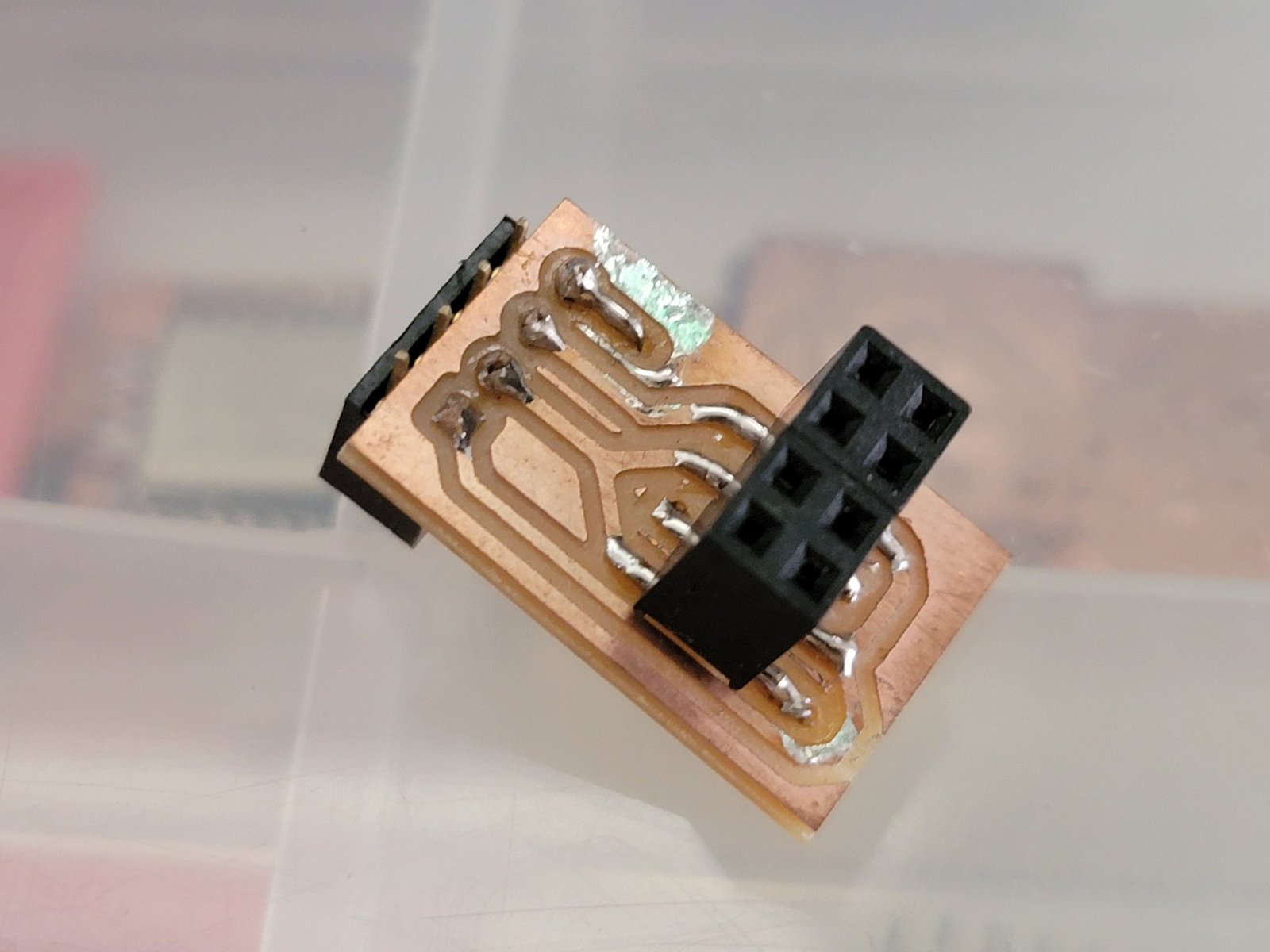
Add-ons - Tails and Stripes
We designed Tigard to use generic pinouts that could easily be adapted to whatever targets you encountered. Some tasks are pretty common, and it makes sense to have a purpose-built wiring harness or adapter.
In full concordance with the guidelines from the Society for Putting Things on Top of Other Things, they need a name, like Beagleboard Capes, GreatFET Neighbors, or Arduino Shields. Sticking with the theme, I’ve unilaterally decided that Tigard add-on boards should be called ‘Stripes’ and customized wiring harnesses should be called ‘Tails’. This means the harnesses that ship with Tigard should be the "UART Tail" and the "JTAG tail". The inexpensive SOIC-8 clips that come with a ribbon cable and 2x4 header will be known as "SOIC8 Tails".
The first Stripe is likely the hastily made ESP-01 programmer I assembled - I won’t release this one but welcome people to submit their own Tails and Stripes via Github Issues.
Applied Physical Attacks Class
Those of you who went all-in on the full Applied Physical Attacks Class will be receiving your kits soon. When you do, there will be an envelope inside with a coupon code you can redeem on the course website. Apply your coupon code, and proceed to checkout. You can make up a name and address, but you need to a valid email address that will be tied you your account for course access. Once you are logged in, you should see the details about the course, as well as the different methods of getting help as you work through the material. Don’t hesitate to ask if you have any trouble.
Future Updates
Now that things are shipping, updates will be less frequent and will focus on interesting uses that all of you come up with for Tigard. Until then, Happy Hardware Hacking!!