NewAE Technology Inc
Security & Privacy
Protocol Interfaces
NewAE Technology Inc
Security & Privacy
Protocol Interfaces
ChipWhisperer-Husky is designed as a compact package for working with side-channel power analysis and fault injection. It builds on our experience with ChipWhisperer-Lite and ChipWhisperer-Pro, adding new features like high-speed logic analyzers (to visualize glitches), real-time data streaming for attacking asymmetric algorithms, support for JTAG/SWD programming with an FTDI-compatible mode, and additional I/O expansion pins. ChipWhisperer-Husky is designed to be highly accessible to researchers while preserving our ability to offer long-term support. This means that, while the entire product is not OSHW-certified, the core—including the FPGA logic, microcontroller firmware, and computer code—is open-source, so you can make modifications and add features.
ChipWhisperer-Husky works with a variety of educational resources we have already built and organized into self-taught "courses". You can see examples of these courses as part of the ChipWhisperer Project. If you need more help, we offer a video series on ChipWhisperer.io, and The Hardware Hacking Handbook has numerous examples that are compatible with ChipWhisperer-Husky.
So what can you do with these resources and a ChipWhisperer-Husky?
ChipWhisperer-Husky is custom designed to perform power analysis & fault injection. It benefits from numerous architecture-level decisions that give you a more stable and reliable experience compared to other off-the-shelf test gear (such as oscilloscopes and function generators). One such feature is synchronous sampling, which means the sample clock of your target device and the sample clock of ChipWhisperer-Husky can be perfectly aligned.
This requires ChipWhisperer-Husky to be able to synchronize to any clock frequency, not just a standard 10 MHz reference like most test gear. We use a PLL chip to provide this feature in ChipWhisperer-Husky. This offers better flexibility than the previous generation, which relied on a PLL block in the FPGA. ChipWhisperer-Husky can of course act like a normal "asynchronous" oscilloscope, instead, allowing you to specify any sample frequency within its range.
The unique design of ChipWhisperer-Husky also lets it generate various glitches, including clock glitches, which may be less than a nanosecond wide:
Generating such a short pulse with a standard function generator would require a unit in the range of 1 GS/s (and an even higher analog bandwidth). Then you’d still need to write all the interface code! And chances that another researcher would have the exact same unit would be low, so you’d struggle to achieve the level of community reproducibility that we designed ChipWhisperer to provide.
Another new feature of ChipWhisperer-Husky is a built-in logic analyzer that you can use to visualize glitches and other digital signals:
Because it was designed specifically for power analysis & fault injection, ChipWhisperer-Husky has a huge range of triggering mechanisms. These mechanisms run "on the hardware" in the FPGA and allow you to trigger on things like:
Level / Edge: Trigger on digital rising or falling edge or when passing a specific analog value. This is the normal triggering mechanism you’ll find in every oscilloscope. To see how it works, have a look at the open-source Verilog core.
Analog Waveform: Trigger when matching a specific pattern in the waveform, not just when crossing a threshold. This allows you to trigger on specific code that you previously identified, even without any external digital signal. This feature was previously exclusive to ChipWhisperer-Pro and certain application-specific products such as Riscure icWaves. You can see how it works in the open-source Verilog core.
UART Bytes: Trigger on a specific UART character, which allows you to time things relative to a specific boot message or as part of a protocol. This is part of the core trigger unit linked above.
Edge Count: Trigger on a number of rising edges, which can be useful to trigger on digital protocols for which no specific decoder yet exists. Learn more in the open-source Verilog core.
Arm Trace: ChipWhisperer-Husky understands the Arm trace format, with messages coming from both SWO (serial trace) and parallel trace pins. This advanced feature—which was designed specifically for white-box evaluations in which you have full control of the target—makes it trivial to understand new algorithms and libraries. The triggering feature means you can trigger when the code hits specific Program Counter (PC) values. This is part of our open-source TraceWhisperer core.
FPGA Fun: Not only is the ChipWhisperer-Husky FPGA design fully open, it supports extensive test benches, including Verilator simulation-based test benches, so you can add new modules and features as well.
ChipWhisperer-Husky ships with two "targets" on which you can run various code, including all of our tutorials. The targets represent typical embedded systems you might be working with when trying to protect against these attacks, and they give you a known starting point so you don’t have to waste time getting the instrumentation setup. Instead, you can jump right into the interesting part of the work: exploring power analysis and fault injection.
The microcontroller-based target is a Microchip SAM4S2A, which has 128 KBytes of FLASH and 64 KBytes of SRAM. It is large enough to run most algorithms you throw at it, including AES, RSA, and ECC.
The other target uses the popular Lattice iCE40 FPGA. We’ve already setup the tutorial to run NEORV32, a soft-core RISC-V processor. This means you can use the iCE40 target as a RISC-V microcontroller target out of the box. You can also run some cryptographic cores on it—an AES core fits, for example—which allows you to perform attacks on hardware-based cryptographic implementations.
If you want more targets, we’ve designed lots over the years. For this Crowd Supply campaign, we’ve added a new, low-cost Artix A35 FPGA target, which is big enough to let you run hardware ECC, and even larger soft-core microcontrollers such as the Arm DesignStart. We’ve also collected a few of our devices that have hardware cryptographic accelerators into one package.
ChipWhisperer-Husky development is found here:
We have not obtained OSHW certification for ChipWhisperer-Husky. Instead, we have focused on producing a highly accessible hardware platform, which requires that we provide long-term support for users. That, in turn, requires us to know that the tools available on the market were produced by us and subject to our quality-assurance process. This approach has allowed us to grow the company while keeping the educational tutorials and critical design pieces (such as the FPGA and firmware code) fully open source.
ChipWhisperer-Husky is a feature and architecture upgrade to the ChipWhisperer-Lite. It offers features that were previously available only in the more expensive ChipWhisperer-Pro and supports the same innovative "synchronous sampling" technology that underpins our ChipWhisperer capture architecture, which allows you to analyze devices well beyond what its low cost would suggest.
ChipWhisperer-Husky includes a substantially upgraded FPGA. It now uses a 7-series model, which makes it easy to use with modern tools. The FPGA code has been entirely redesigned with the help of our FPGA wizard, J-P, who uses actual test benches (unlike Colin).
You can see a comparison between a few of our existing tools, along with other off-the-shelf equipment here:
| ChipWhisperer-Husky | ChipWhisperer-Lite | ChipWhisperer-Nano | Oscilloscope | |
|---|---|---|---|---|
| Open-Source | SW, FW, FPGA | SW,FW,FPGA,PCB | SW,FW (no FPGA) | No |
| Software Support | Python3 API, Python + Jupyter Tutorials | Python3 API, Python + Jupyter Tutorials | Python3 API, Python + Jupyter Tutorials | API (if you're lucky), control software |
| Documentation | Tutorials, API, User Guide | Tutorials, API, User Guide | Tutorials, API, User Guide | API only (maybe), user guide |
| Enclosure | Yes | No | No | Yes |
| QA managers | Canine | Canine | Canine | Human |
| ADC | ||||
| Sample Clock Mode | Synchronous or Async | Synchronous or Async | Synchronous | Asynchronous |
| Sample Clock to Device Clock Ratios | Arbitrary | Fixed | Fixed | N/A |
| Sample Clock phase shift adjustment | Yes | Yes | No | N/A |
| Max Sample Rate | 200¹ MS/s | 105¹ MS/s | 20¹ MS/s | >100 MS/s |
| Bit Depth | 12 bits | 10 bits | 8 bits | 8 bits (most common) |
| Sample Buffer Size | 100 KSample | 24 KSample | 80 KSample | 16 KSample - 4 GSample |
| Segmented Capture | Yes | Beta Feature | No | Depends on scope |
| Streaming Mode (Unlimited capture size) | Yes | No | No | Depends on scope |
| Trigger Mode | Edge,Level,Pattern,UART,Arm SWO,Arm Trace,Custom FPGA | Edge,Level | Edge | Edge,Level,sometimes others |
| I/O | ||||
| JTAG/SWD Support | Yes | Yes | Partial | No |
| Arm ETM Support (Trace Capture) | Yes | No | No | No |
| USB-Serial Support | Yes | Yes | Yes | No |
| Logic Analyzer Mode | Yes, 300 MS/s | No | No | Sometimes |
| Programming Support (Native) | STM32Fx, AVR, XMEGA, iCE40, Xilinx FPGA | STM32Fx, AVR, XMEGA, iCE40, Xilinx FPGA | STM32Fx, AVR, XMEGA | None |
| Programming Support (via OpenOCD) | Any supported JTAG/SWD device | Any supported JTAG/SWD device | Any supported JTAG/SWD device | None |
| Auxiliary Output Connector | Yes | Not Mounted | No | Sometimes |
| Glitch | ||||
| Clock Output | Yes | Yes | No | No |
| Voltage Output | Yes | Yes | Partial | No |
| Aux Output | Yes | Partial | No | No |
| Visualizer/Monitor | Clock+Voltage | Voltage | Voltage | N/A |
| Glitches per Trigger | Multiple | Single | Single | N/A |
| Cost USD | $549 | $300 | $50 | $200 - $5000 |
¹ Max ADC specification - in practice, max sample rate is 1.1x to 2x this, depending on the environment
ChipWhisperer-Husky uses a new "target" design that plugs in on an edge connector. We call this style the "CW312" (or often written as CW312T, for ‘CW312 Target’). This makes it easier to build targets by avoiding the through-hole soldering the old version required (the new style uses the edge connectors, the old style has the 3 rows of 20-pin male headers)
You can convert between the two using the adapter board, which allows soldering of a "CW308" style target onto an interposer board:
In addition, you might want the CW308 "UFO Board". This was our original base-board (read more about it here), which provides some additional features, including better I/O protection against ESD or aggressive glitching (such as when using EMFI), more power-supply options, and better filtering. Due to supply-chain challenges we’ve delayed the replacement of the CW308, and instead use it alongside the "CW313" board that ships with ChipWhisperer-Husky:
All of the ChipWhisperer capture solutions use the same 20-pin connection pinout. This means you can sub ChipWhisperer-Husky into existing kits or tutorials with little effort.
Currently, more targets are available in the CW308 style than the CW312 style. The "CW312" board—the planned replacement for the CW308—doesn’t exist yet. Instead what ships with ChipWhisperer-Husky is the CW313 "interposer", which includes several headers but a more limited set of active components (only voltage regulators & LEDs).
We all know that component sourcing is not easy these days, which might make you wonder why we are launching a new tool right now. We’ve been working hard to ensure the ChipWhisperer-Husky has a relatively agile design. To that end, we have secured future deliveries of core components (such as FPGAs and microcontrollers) for at least 400 units. We’ve even done some small runs to ensure we can deliver orders as fast as possible.
NOTE: Once we run out of our pre-stocked parts, we may find ourselves looking at a very long lag. ChipWhisperer-Husky’s core FPGA is currently facing lead times of at least a year. We do have orders in, but they will take some time to arrive. Estimated delivery timelines for crowdfunding backers are based on our existing inventory. We may fulfill orders in multiple batches, and you can expect that some deliveries will likely occur sooner than others. (In particular, the first 20 to 40 backers might receive their boards early thanks to our existing stock of assembled boards.)
We’ll have more updates as the campaign progresses.
ChipWhisperer-Husky will be manufactured by long-term PCBA partners with whom we’ve worked for many years (including to deliver PhyWhisperer-USB). Most of the final testing and packaging will be done on-site in our production facilities here, which have slowly grown over the years and now look rather like a legitimate office:
Our Assistant (to the) QA Manager, Bergen, who you first met in the PhyWhisperer-USB campaign, has been keeping a close watch on everything to ensure the QA Manager (Luna) isn’t fully overloaded.
Luna, our QA Manager, and Bergen, Assistant (to the) QA Manager.
NewAE Technology Inc. has been selling hardware on the interwebs for the past eight years, so we’re no stranger to the hassles of logistics. Fulfillment will be handled by Crowd Supply and Mouser, who have plenty of experience delivering products all over the world.
ChipWhisperer-Husky will be subject to CE testing to ensure distribution in European markets. We’ve done such tests on other products, including ChipWhisperer-Lite, so we do not foresee any major issues. We anticipate the need to make at most a few minor board tweaks.
NOTE: The hardware cryptographic target pack will likely be subject to export restriction due to it’s inclusion of hardware cryptographic accelerators. If you order this product, you might need to provide additional information to receive it! ChipWhisperer-Husky itself does not include any such restricted technology, and we’ve been careful to avoid including hardware-based cryptographic targets that might trigger such restrictions on other products.
WARNING: See the note in Component Sourcing. We expect to have variable delivery times due to batching the production process. The specified estimates apply to the first batches.
Supply-chain delays and chip shortages have been a global concern over the past couple of years. This campaign was originally planned for a fall 2021 launch but was delayed to ensure the solidity of our supply chain. The good news is, we’ve already manufactured an initial run of ChipWhisperer-Husky boards, and we’ve had numerous beta and R&D units out in the field for the past 18 months. In addition, thanks to our supplier relationships and to the cash-flow generated by our previous products, we have:
Finally, we have taken full advantage of recent delays to complete all of the "planned" features for ChipWhisperer-Husky. The risk risk of "R&D problems" is even lower than usual, and the product you receive will be fully feature-complete!
"The Canadian-based security research company NewAE Technology is announcing their latest side-channel attack tool, the ChipWhisperer-Husky."
"Developers, engineers and hobbyists may be interested in a new compact device specifically designed for experimenting with side-channel power analysis and fault injection."
"[The] device delivers a more stable and reliable experience compared to other off-the-shelf test gear such as oscilloscopes and function generators thanks to features such as synchronous sampling..."
Produced by NewAE Technology Inc in Halifax, NS, Canada.
Sold and shipped by Crowd Supply.
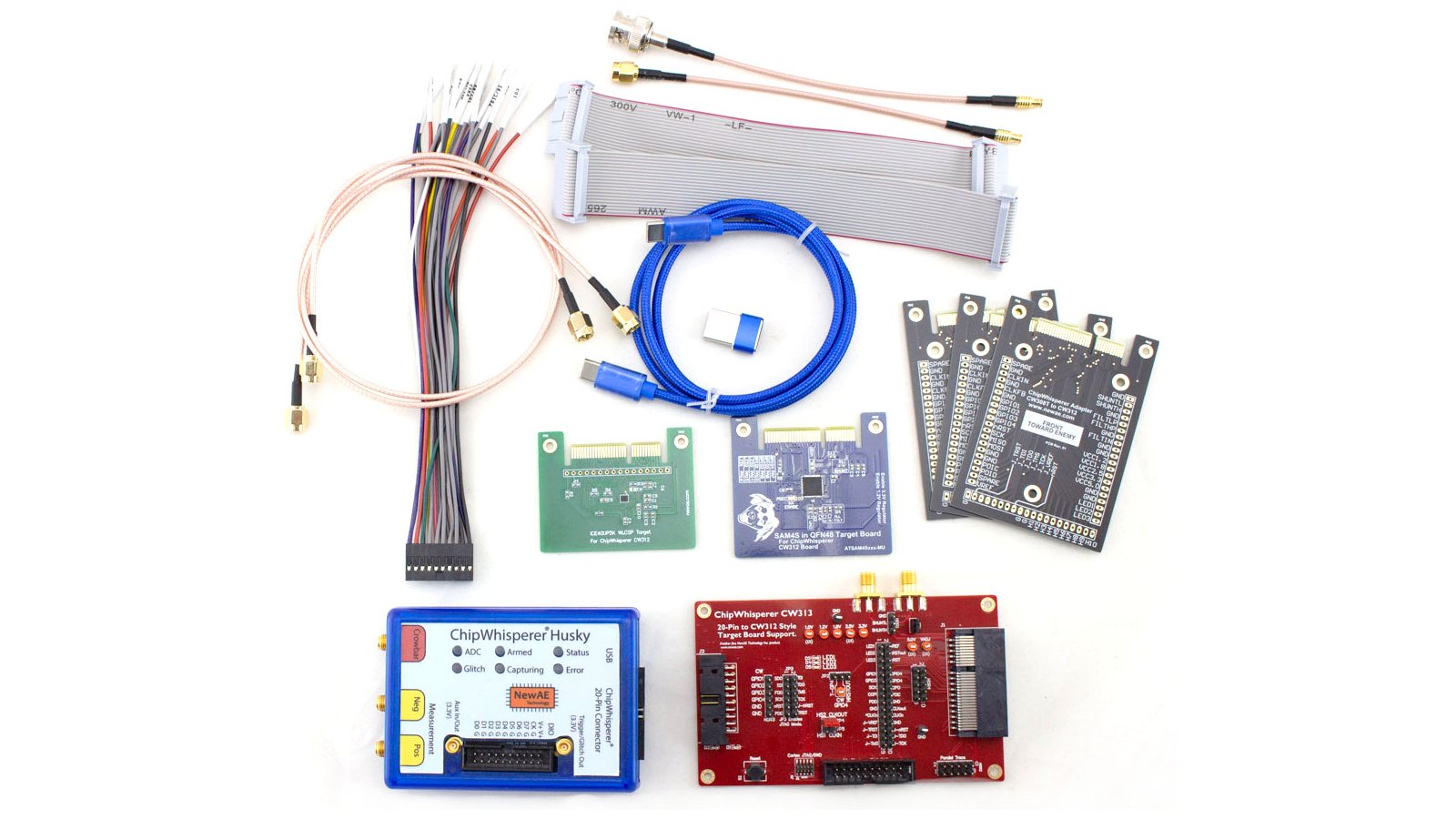
Run most of the ChipWhisperer tutorials, including power analysis, clock glitching, and voltage glitching. Includes ChipWhisperer-Husky unit, CW313 target base-board, iCE40 (small FPGA) target, SAM4S (Arm processor) target, USB cables, SMA cables, 20-pin straight-through and breakout cables

A selection of targets with hardware cryptographic features, which allow you to perform more advanced power-analysis attacks, includes SAM4L, SAM11L, EFR32MG32A, and MK82F. Targets are in both CW308 and CW312 form factors.
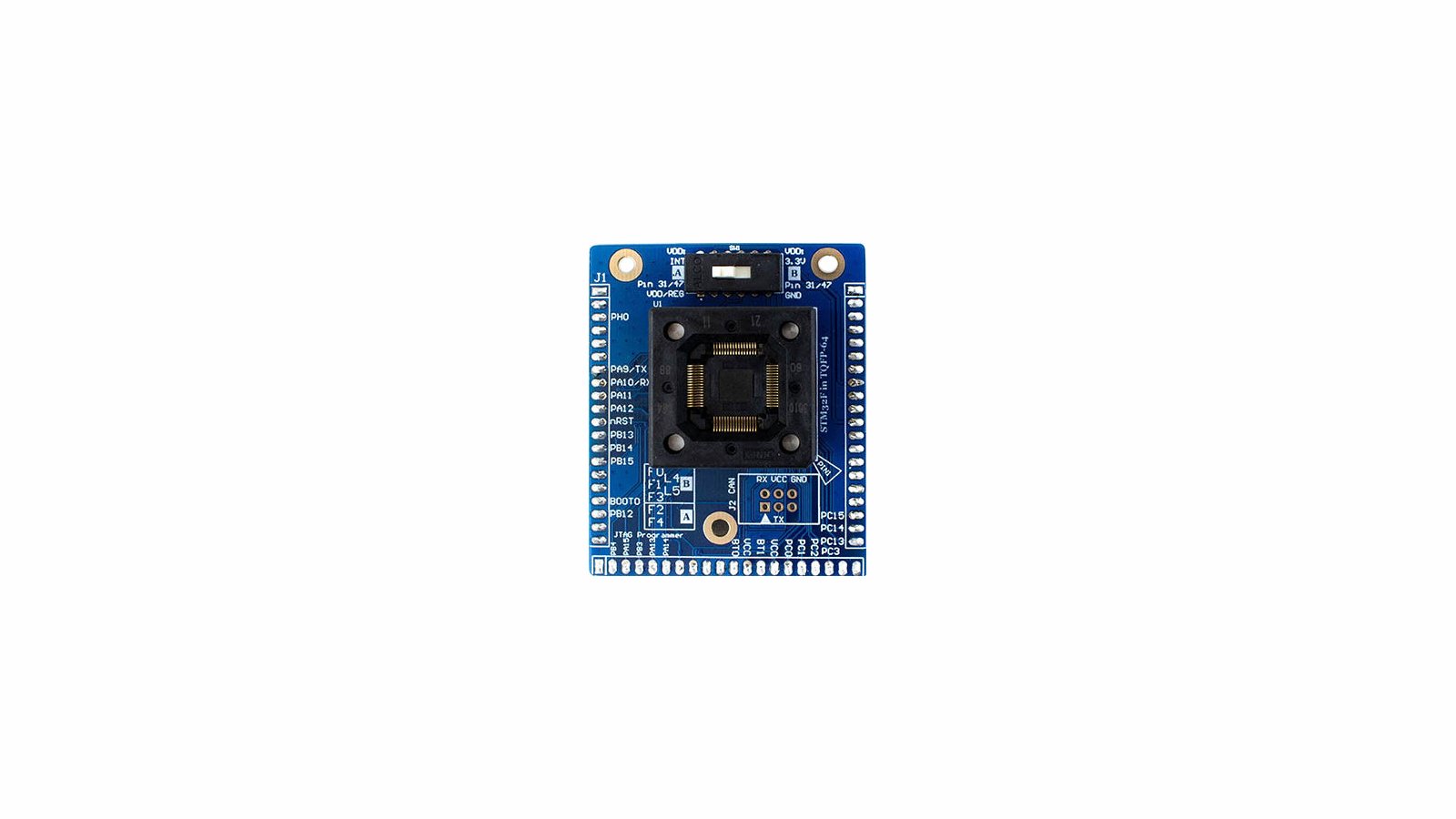
A TQFP64 socket that fits most STM32F0/1/2/3/4 microcontrollers (along with GigaDevice compatable pinouts). Great for performing research on multiple devices and testing how resiliant templates are.

5x CW312 Breakout/Adapter PCBs
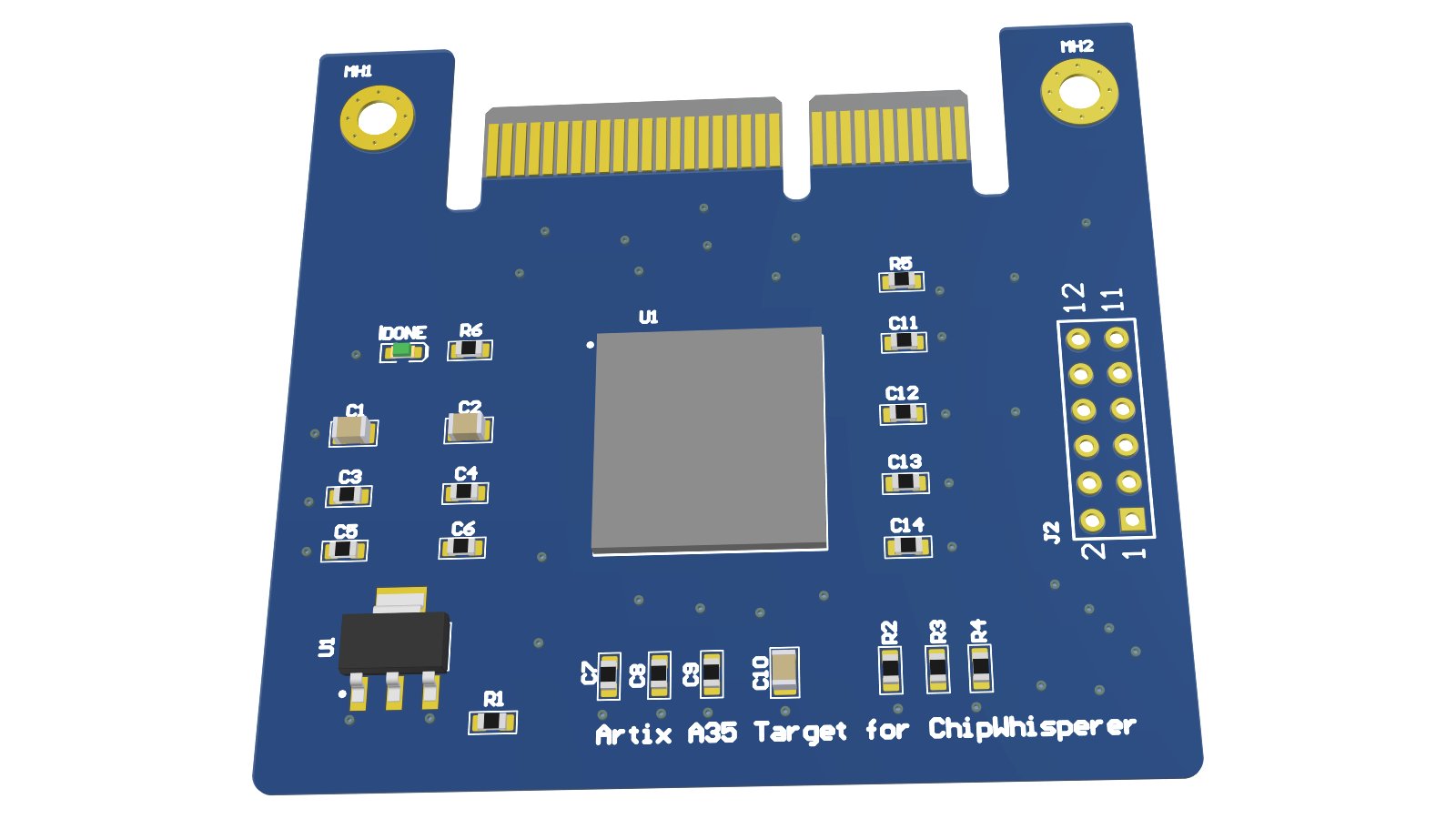
Artix A35 FPGA target, allows implementation of larger cryptographic cores than fit in the small iCE40 target.
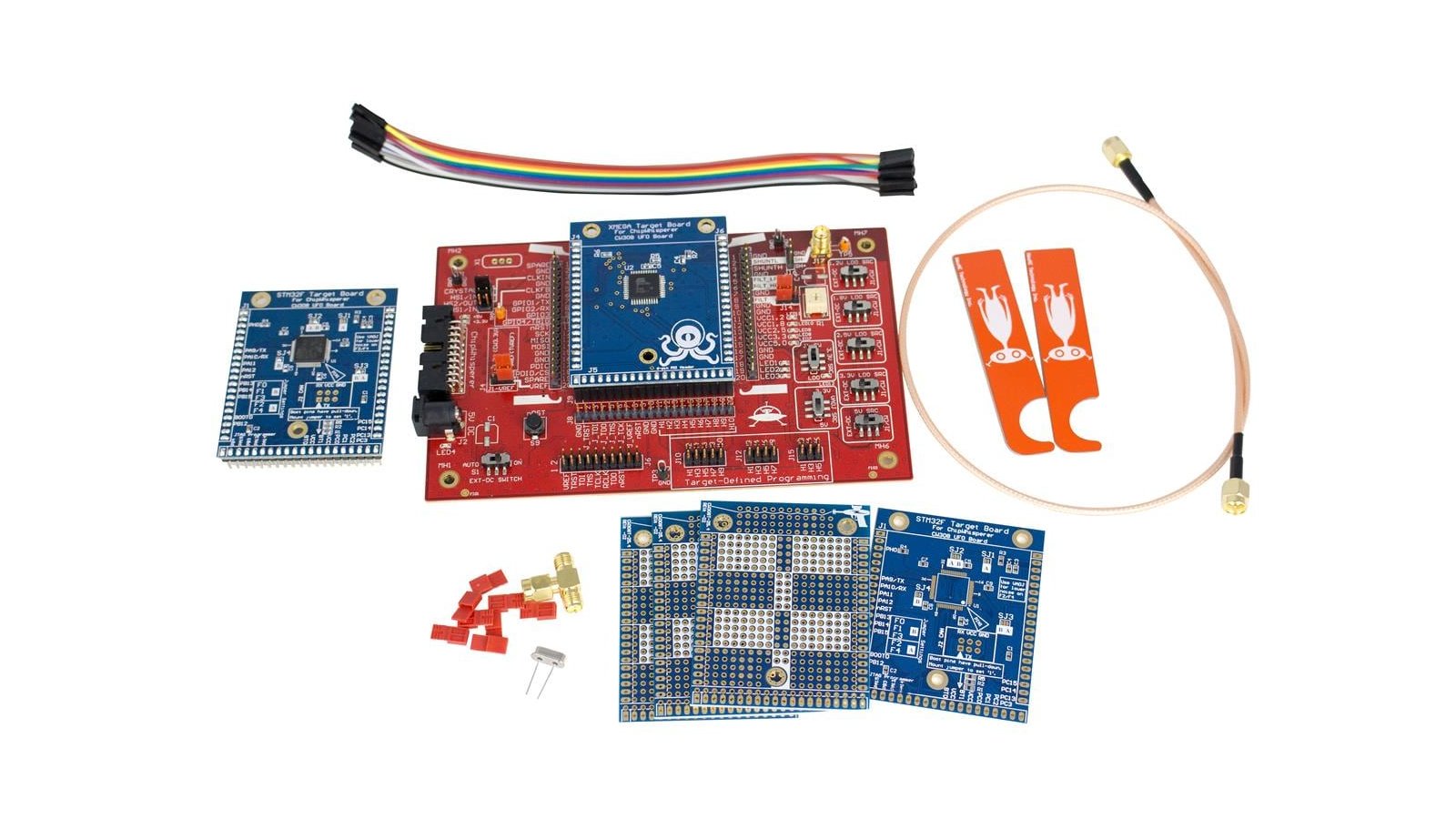
From the ChipWhisperer Target Boards project.
The CW308 puts all the standard requirements onto one board (such as power supplies, oscillators, filters) allowing you to make super-simple hardware-hacking target boards.

From the The Hardware Hacking Handbook project.
Learn how to break embedded security with hardware attacks with this 512-page No Starch Press book by Colin O'Flynn and Jasper van Woudenberg. You will receive the printed book and free access to the PDF, Mobi, and ePub digital versions.

NewAE developed the ChipWhisperer, the first open-source tool for side-channel power analysis and fault injection. They have shipped over 2000 of their low-cost boards & now offer a wide range of products to help embedded designers evaluate and develop embedded hardware security solutions.