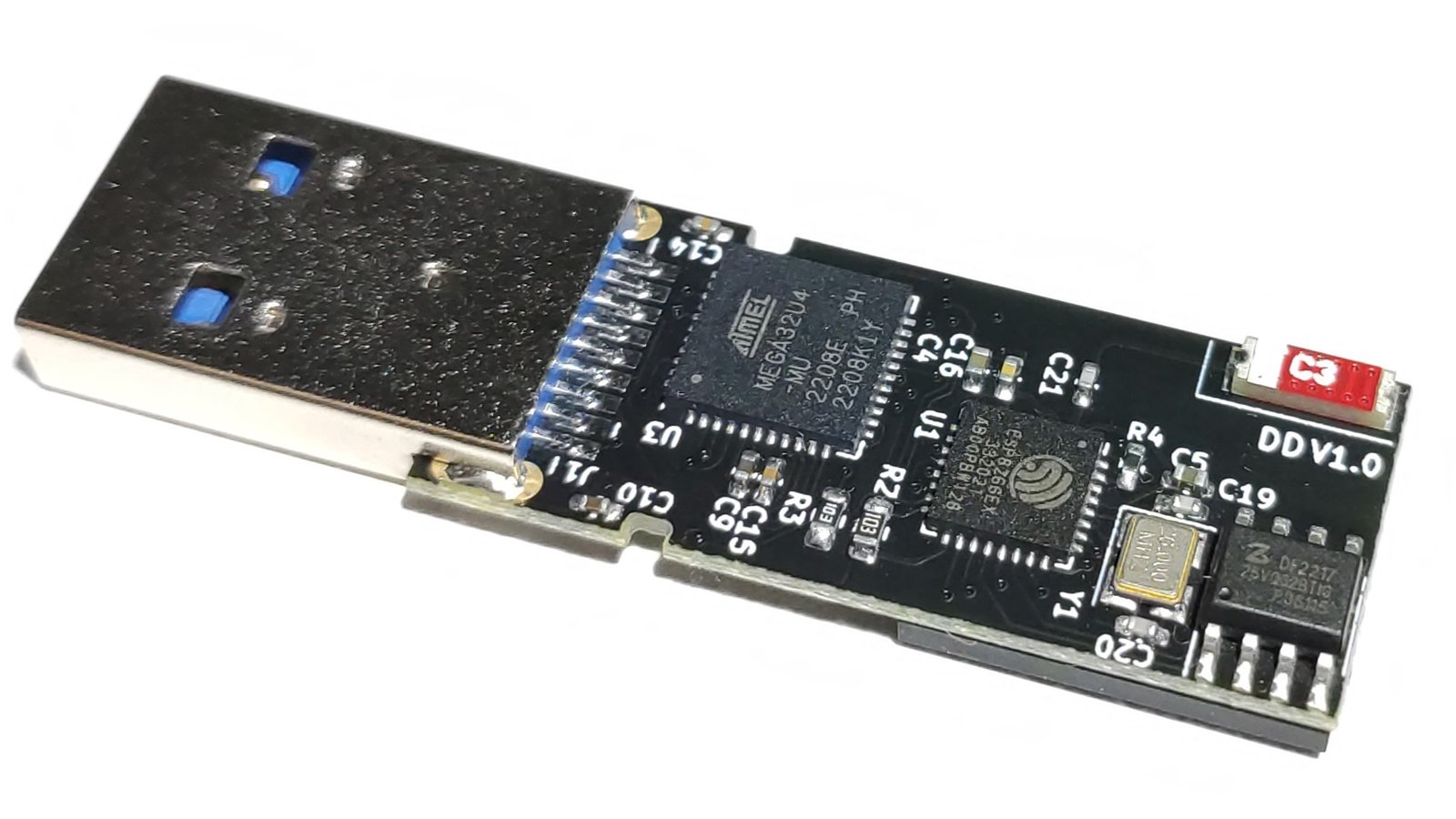
Diabolic Drive is a stealthy, wireless keystroke-injection tool that can send payloads over Wi-Fi while disguised as a regular 64 GB USB flash drive. Diabolic Drive is excellent for use in cybersecurity, particularly when red teaming, as it behaves like a typical flash drive until it is wirelessly instructed to deploy keystrokes.
Diabolic Drive adheres to the standard form factor of a "universal" USB drive, allowing it to be easily concealed with an inconspicuous flash-drive enclosure. When plugged in, anyone can interact with it like a normal flash drive, and it performs just like a genuine device, with average read speeds of up to 20 Mbps and write speeds of up to 10 Mbps. This behavior helps mask its wireless keystroke-injection features. Diabolic Drive is the first off-the-shelf product that combines all of these features into a single device. As such, it opens up untold social engineering attack possibilities.
Diabolic drive can be accessed remotely over Wi-Fi. Fire your payload remotely and precisely, or pre-program the drive to deliver keystrokes when plugged in.
When plugged into a host, Diabolic Drive acts like a regular USB flash drive, including any audio notifications that would normally occur. Even when it’s configured to identify itself as a flash drive, a human-interface device (HID), and a virtual COM port simultaneously, it triggers only a single audio notification, which is how a standard flash drive would behave. (The COM port allows you to program Diabolic Drive using the Arduino IDE, and you can disable it with "Stealth Mode" for actual red-team engagements.)
By default, Diabolic Drive enters the "spectre" state, after it’s plugged in, rather than going "active" immediately. As long as it remains in that state, it appears only as a flash dive…right up until you deem it safe to expose the HID interface and begin injecting keystrokes, at which point you can initiate the attack remotely over a Wi-Fi connection! Until then, the HID interface is completely dormant, with no unexpected behavior to detect and no abnormal logs generated.
For maximum stealthiness, Diabolic Drive allows you to spoof the identifying information it presents when connecting as a flash-storage device and as a human-interface device (HID). For flash storage, this includes the vendor ID (VID), the product ID (PID), vendor info, product info, rev info, the vendor string, the product string, and the serial number (SN), which makes it extremely challenging to distinguish Diabolic Drive from a regular flash drive. For the ATmega32U4 HID, you can spoof the VID and PID of an HID that was previously connected to a particular target computer in order to avoid a pop-up notification about the installation of a new keyboard when Diabolic Drive exposes its HID interface.
Diabolic Drive was designed for maximum capability and stealth, with an eye toward openness, flexibility, control, and future proofing. It contains the following components:
| Diabolic Drive | Rubber Ducky | O.MG CABLE Basic | USBNinja | |
|---|---|---|---|---|
| Form Factor | Flash drive | USB stick | USB cable | USB cable |
| USB Type-C Availability | No | Yes | Available | Available |
| Flash Storage | Yes (64 GB) | No | No | No |
| Self-Destruct | No | No | Yes | No |
| Keystroke Reflection Exfiltration | No | Yes | No | No |
| Wireless Control | Wi-Fi | No | Wi-Fi | Bluetooth |
| Payload Over the Air (OTA) | Yes | No | Yes | No |
| OTA Firmware Upgradable | Yes | No | No | No |
| Different Enclosures Support | Yes | No | No | No |
| Price | $107 | $79.99 | $119.99 | $99 |
Upload Arduino Sketches by directly plugging your Diabolic Drive into your computer, as ATmega32U4 has native USB support through a built-in USB transceiver that handles the USB connection.
This unique bootloader feature gives you full control over Diabolic Drive’s ATmega32U4 through the USB 3.0 pins. By default, Diabolic Drive uses a modified version of the Arduino Leonardo bootloader. It is also compatible with the original Arduino Leonardo bootloader.
You can find project information, programming instructions, design files, and a list of firmware options in our GitHub repository.
Produced by UNIT 72784 in Cairo, Egypt.
Sold and shipped by Crowd Supply.
stealthy wireless keystroke injection tool with 64 GB storage

Cybersecurity hardware company developing unique Red Teaming and Penetration Testing hardware devices.