SoloKeys
Security & Privacy
*omu
SoloKeys
Security & Privacy
*omu
Somu is a tiny FIDO2 security key you can use with your Google, Twitter, and GitHub accounts for two-factor authentication, or your Microsoft account for passwordless login. Somu fits in your USB port, so you’ll never forget your key again.
Somu is the micro version of Solo. We were inspired to make a secure Tomu, so we took its tiny form factor, we added the secure microcontroller and firmware of Solo, et voilà! Here we have Somu.
Somu and all our other keys share open source hardware and firmware, because we believe that security should be more open, especially when it comes to hardware. Our keys are verified, trustworthy and hide no secrets. Well, except one: a master secret is safely stored and protected by the STM32 microcontroller, so that only you can log in, of course.
A note on security: in this campaign, we’re only selling Somu Hacker, the reprogrammable version of Somu. Please read the details in the section "Somu Hacker and Security" below.
Like many other FIDO2 security keys on the market, Somu works seamlessly with your Google, Twitter, and GitHub accounts for two-factor authentication, or with your Microsoft account for passwordless login. Somu fits in your USB port, so you’ll never forget your key again. And FIDO2 / WebAuthn is now a web standard, so you don’t need any extension whatsoever, Somu just works on most operating systems and browsers.
Unlike many other FIDO2 security keys on the market, Somu is fully open source and reprogrammable. It has an STM32L4, one RGB led, and two buttons. It’s secure against online attacks and can be permanently locked down to be secure against physical attacks (more on firmware security below).
Development is already in progress, but the space is pretty fragmented with many lacking features from other tools (for example, ssh-agent/opensc lack support for Ed25519). For these reasons, a stretch goal seemed appropriate. With some extra funding, we can certainly speed up development, including submitting PRs to other projects. And if you’d like to be more involved, feel free to jump on GitHub!
Because Somu fits entirely in your USB port, it’ll soon become your inseparable companion for all your projects. Those (maybe low-levelish) projects, which before required space, extra devices, and wires all over the place… can now be worked on anywhere that you are! Here are some ideas:
We talk a lot about hardware and firmware, but let’s not forget the basics. WebAuthn is now a W3C standard, supported in all major browsers and OS’s, and offers stronger authentication than plain username+password. With Somu, you can test WebAuthn with just a few lines of JavaScript in your website, and build support for two-factor authentication, passwordless login, and even extra verification for sensitive user actions within your app (e.g., confirming transactions or critical changes to the settings).
You can use Somu to prototype or build applications that interact with a secure hardware component. Using WebAuthn extensions, you can build web apps that run in the browser and interact with Somu for functionalities other than pure authentication. For example, to digitally sign a document or a transaction. And because Somu is open source, you can even add new FIDO2 extensions to its firmware to expand its capabilities and then immediately use them within your app.
With one RGB LED and two buttons, Somu is a great STM32 board with a good amount of real-world code to tweak and learn from. You can also run Arduino on Somu via the STM32duino project. In both cases, you can access the entire spectrum of features of the STM32 in C/C++ (or even Rust), and not be limited by a Java card abstraction.
We have two different flavors for all our security keys, including Somu: "secure" for consumers, and "hacker" for developers.
In this campaign, we’re only selling Somu Hacker, the reprogrammable version of Somu (with the exception of the highest pledge value, for which you can choose any combination of Somu Hacker or Somu Secure—on the assumption you’ll want to resell the keys to consumers).
Both Somu Secure and Somu Hacker, like any security keys, are secure against online attacks, including account takeover and phishing.
Somu Secure has locked-down firmware, and you can only upgrade it with firmware released and signed by us.
Somu Hacker is unlocked and reprogrammable by design. Because of that, a potential malware on your laptop may rewrite its firmware. At anytime, you can permanently lock Somu Hacker down, and make it de facto a Somu Secure. (The opposite is not possible - a Somu Secure may never become a Hacker)
If an attacker physically steals your key, they can simply use it. So physical attacks are generally not considered by FIDO. This said, you can set a PIN for your security key, and we use STM32 level 2 readout protection to ensure that secrets never leave the device - thus ensuring that an evil butler can’t clone your key.
Also note that malware could potentially compromise many things in your system - such as your browser pr your DNS cache (important against phishing attacks). So while it’s clear that Somu Secure is strictly more secure than Somu Hacker in theory, in practice, it’s hard to define where the line is. In general, to stay safe, we don’t recommend using Somu Hacker for production.
| Somu | Tomu | Yubikey Nano 5 | Yubikey Nano 4 | Solo | |
|---|---|---|---|---|---|
| Tiny | Yes | Yes | Yes | Yes | No |
| **Secure*** | Yes | No | Yes | Yes | Yes |
| Open Source | Yes | Yes | No | No | Yes |
| U2F | Yes | Yes | Yes | Yes | Yes |
| FIDO2 | Yes | No | Yes | No | Yes |
| Buttons | 2 | 2 | 1 | 1 | 1 |
| LEDs | RGB | R+G | RGB | RGB | RGB |
| Made in | Italy | China | US / Sweden | US / Sweden | Italy |
| Retail Price | $35 | $30 | $50 | n/a | $20 |
* The microcontroller supports security features to protect against physical extraction of key material
The PCB is a one mm thick two-layer board, with Z-axis milling. The milling makes the short tabs on the sides allow the PCB to "slide fit" into the case.
The edge that protrudes (slightly) out of your USB port is plated to make two independent capacitive touch buttons. Firmware will currently combine and treat them as one, but they may be configured for two different actions in the future.
Similar to Solo, the case is a durable silicone sleeve, which will flex slightly around the PCB to make a good fit.
We’re pretty actively working on firmware development on GitHub, you can join the discussion, submit PRs, or just lurk around and learn about our project or FIDO more generally. We want to add support for SSH/GPG, to which you’re very welcome to contribute.
We also noticed that the space is fragmented and many features are lacking from other tools. For example, while OpenSSH supports Ed25519 and we could add support to our firmware, connecting the dots isn’t as straightforward as it seems. Neither OpenSSH agent (the client) nor OpenSC (the PKCS11 driver) support Ed25519. Any help to add support for Ed25519 in OpenSSH agent and OpenSC is greatly appreciated.
And of course, if you have any other ideas on things you want to make with Somu, please don’t hesitate to get in touch below or reach out on Twitter @SoloKeysSec… this is the beauty of open source!
You can find more about SoloKeys at https://solokeys.com, and if you have any specific questions, feel free to reach out just below. If you want to take a look at the code and current documentation, you can start at https://github.com/solokeys/solo.
Produced by SoloKeys in Laurel, MD.
Sold and shipped by Crowd Supply.

An open source 2FA, FIDO2 security key that fits inside your USB Type-A port.

An open source 2FA, FIDO2 security USB Type-A key fob that is NFC capable.

An open source 2FA, FIDO2 security USB Type-C key fob that is NFC capable.


A hardware-based USB 2.0 monitor & trigger platform, controlled from Python
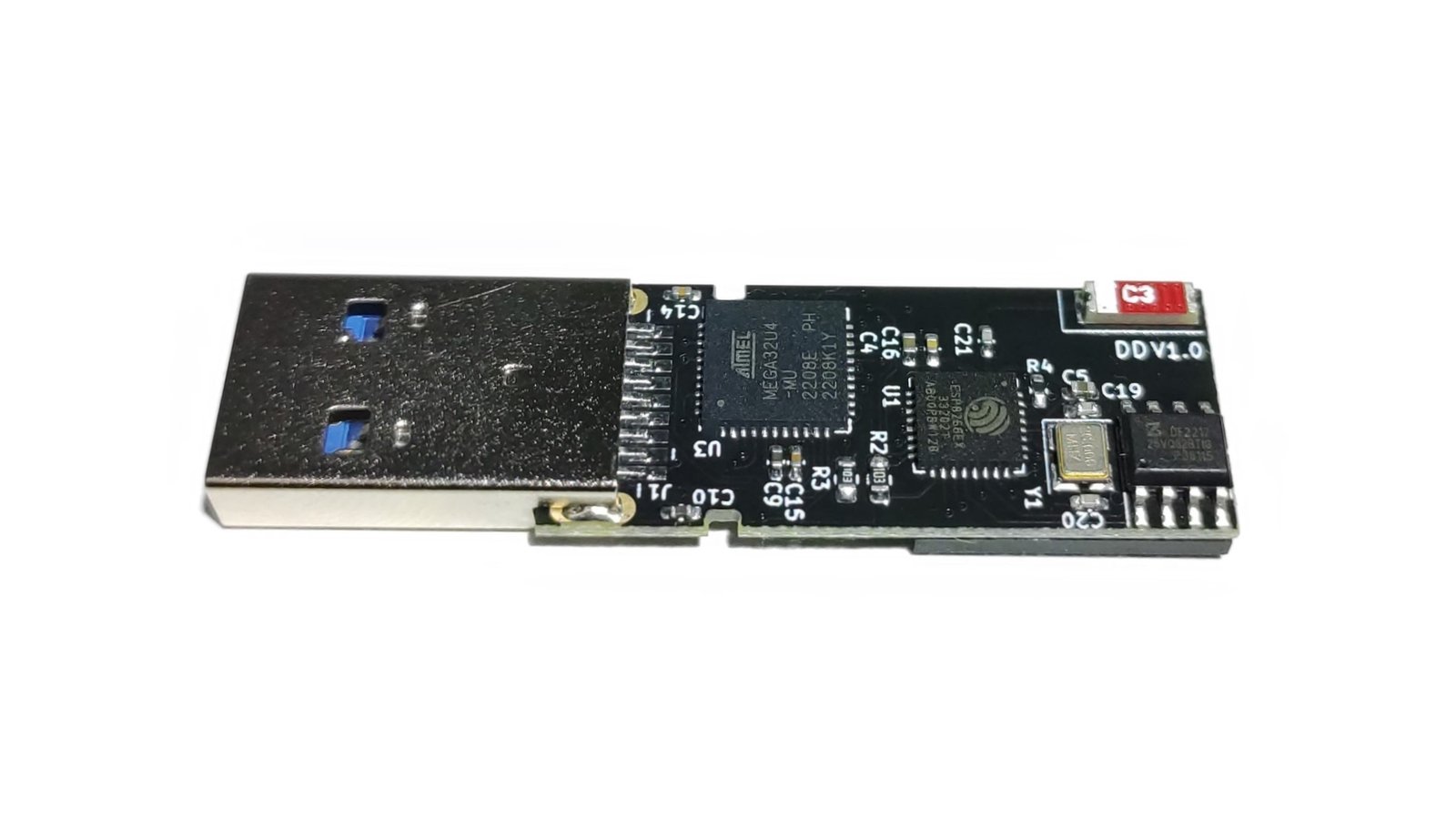
Stealthy, modern, wireless keystroke-injection tool in a universal, four-layer, double-sided flash-drive PCB form factor with 64 GB of storage
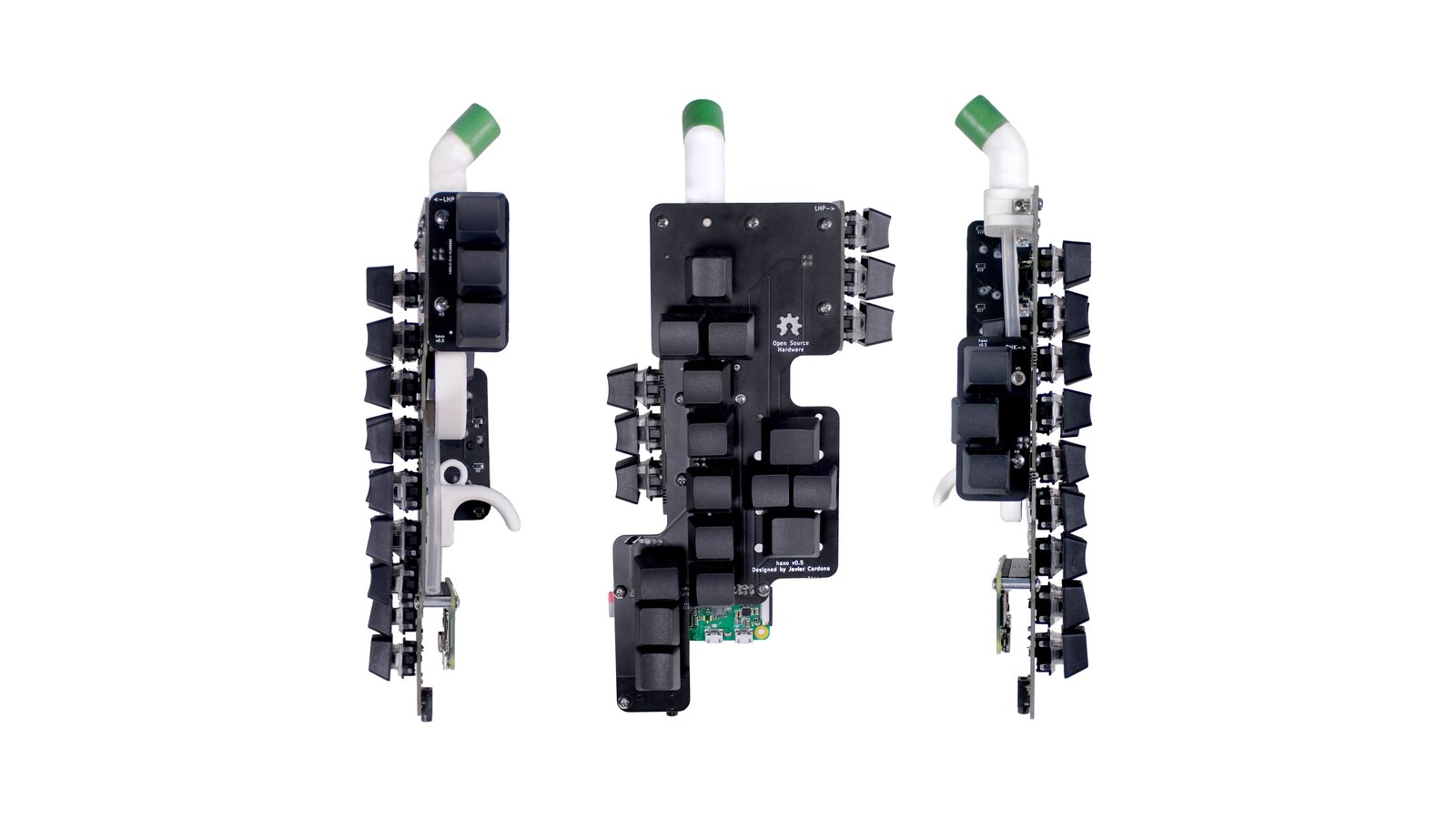
A hackable electronic saxophone with mechanical keys